Important Computer Awareness Materials (Day-27) – Internet Technologies – Important Terms:
Dear Readers, IBPS Exams are approaching shortly, we all knew that Computer Awareness is one of the important section, which will help you to increase your score easily.
Many of our followers were asking us to provide Important Computer Awareness Notes along with the model questions, here we have planned to provide the Topic wise Important Computer Awareness Materials on Daily basis, and also we will provide MCQs based on these topics daily. Kindly follow us regularly and make use of it.
Internet Technologies – Important Terms
Popular Domain names:
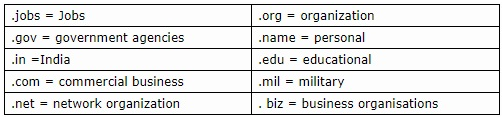
URL has three parts
(i) the protocol to be used to access the file = {http://}
(ii) the IP address = {www.gmail}
(iii) the domain name = {.com}
In other words, encryption is ‘encoding’ any message/information so that only authorizes people can read it. Encryption is done with a private key.
Thus, decryption is the ‘decoding’ of the encoded message, with the help of a public key.
Internet Attack Methods:
a). Eavesdropping:
Interception of communications by an unauthorized party is called eavesdropping. Passive eavesdropping is when the person only secretly listens to the networked messages. On the other hand, active eavesdropping is when the intruder listens and inserts something into the communication stream. This can lead to the messages being distorted. Sensitive information can be stolen this way.
b). Viruses:
Viruses are self-replication programs that use files to infect and propagate [8]. Once a file is opened, the virus will activate within the system
c). Worms:
A worm is similar to a virus because they both are self-replicating, but the worm does not require a file to allow it to propagate . There are two main types of worms, mass-mailing worms and network-aware worms. Mass mailing worms use email as a means to infect other computers. Network aware worms are a major problem for the Internet A network-aware worm selects a target and once the worm accesses the target host, it can infect it by means of a Trojan or otherwise.
d). Trojans:
Trojans appear to be benign programs to the user, but will actually have some malicious purpose. Trojans usually carry some payload such as a virus.
e). Phishing:
Phishing is an attempt to obtain confidential information from an individual, group, or organization. Phishers trick users into disclosing personal data, such as credit card numbers, online banking credentials, and other sensitive information.
f). IP Spoofing Attacks:
Spoofing means to have the address of the computer mirror the address of a trusted computer in order to gain access to other computers. The identity of the intruder is hidden by different means making detection and prevention difficult. With the current IP protocol technology, IP-spoofed packets cannot be eliminated.
Click Here for Computer Awareness Materials (Day-1 to Day-26)
This post was last modified on July 4, 2020 2:16 pm